MANAGED 24/7
WEB APPLICATION FIREWALL SERVICE
AccessQuint’s Cloud WAF Service provides enterprise-grade, continuously adaptive web
application security protection. We offer full coverage of OWASP Top-10 threats and
automatically adapts protections to evolving threats and protected assets.

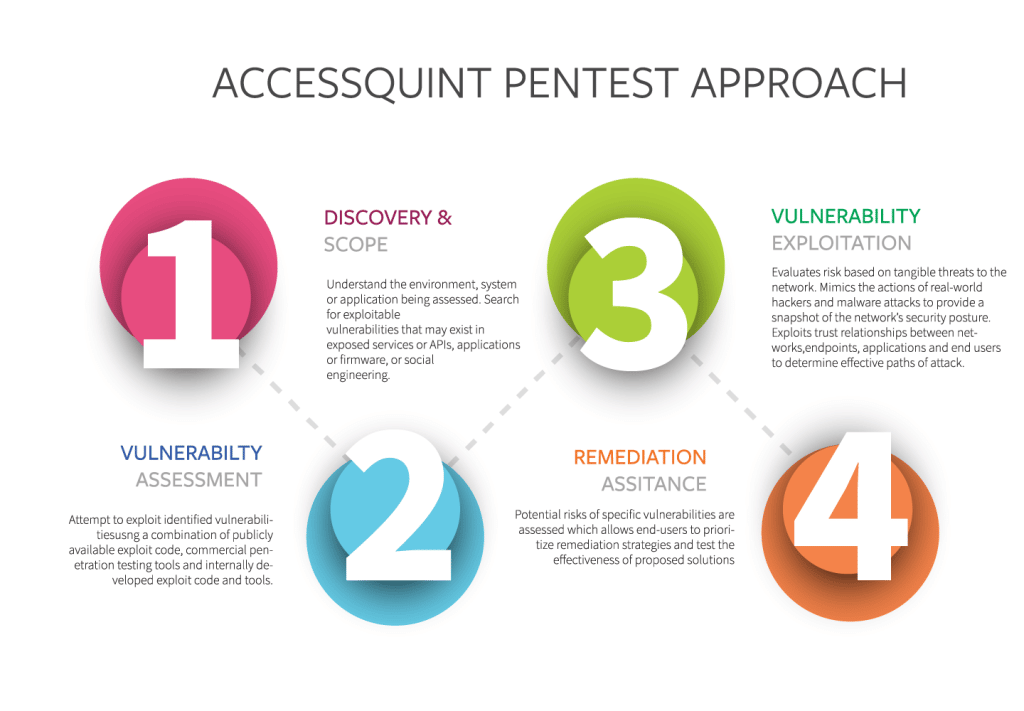
External Pentest
Identify and exploit vulnerabilities on systems, services and applications exposed to the Internet .

PENTEST 02
Internal Pentest
Simulate a malicious insider or an attacker that has gained access to an end-user system, including escalating privileges, installing custom-crafted malware or exfiltrating faux critical data

PENTEST 03
Web Application Pentest
Comprehensively assess web applications for vulnerabilities that can lead to unauthorized access or data exposure and develop a comprehensive framework for assessing the security of web-based applications.

PENTEST 04
External Pentest
Comprehensively assess the security of mobile devices and installed applications on on all mobile platforms, including iOS, Android, and Windows. Leverages OWASP Mobile Top 10 and methodologies to assess the security.

PENTEST 05
API Pentest
Comprehensively assess the security of API structures, understand request methods, understand responses and use techniques to apply to endpoints and exploit bugs on a real production

PENTEST 06
Wireless Pentest
Assess the security of your deployed wireless solution (e.g., 802.x, Bluetooth, Zigbee, etc.). AccessQuint's penetration testers attempt to exploit weaknesses in your network to gain access to privileged areas and demonstrate the potential impact of a wireless network breach.
WEB APPLICATION FIREWALL
ASSESSMENT SERVICE
Applications are the lifeblood of business, so it’s imperative to have an agile security program in place to protect them. With your organization constantly evolving, new or enhanced applications and technology, increased network traffic, data center consolidations, and key business initiatives can strain your infrastructure. Our Web Application Firewall (WAF) solution can help safeguard your data, enable compliance, and provide ongoing protection against application threats.
- PHASE 1: Prepare and Plan
- PHASE 2: Analyze
- PHASE 3: Report
- PHASE 4: Remediation Assistance
1 Prepare and Plan
AccessQuint's WAF consultant works with you to understand your business goals, flag deployment dependencies, capture device details, and set a solid foundation for the analysis.
2 Analyze
During this phase of the process, Our consultant assesses your current WAF configuration and offers recommendations in the following areas:
3 Report
We will consolidate the results into a custom written report specifically for you that details the findings and leverages the expertise of our consultants who intimately understand the WAF solution and its operation, configuration parameters, and future evolution. We will also document any recommended practices identified as productivity enhancements that would benefit your organization.
4 Report
Potential risks of specific vulnerabilities are assessed which allows end-users to prioritize remediation strategies and test the effectiveness of proposed solutions
BUILD SECURE, HIGH-QUALITY SOFTWARE FASTER
BENEFITS
Visibility: Simple, Easy-to-Read Reports
Control: Effective Response and it adds a layer of enriched data that gives context and clarity into application behavior.
Precision: Intelligent Decision-Making
A comprehensive review of your Web Application Firewall configuration by an F5 Professional Services expert
Guidance on how to align business requirements with features available in your F5 Web Application Firewall solution


BUILD SECURE, HIGH-QUALITY SOFTWARE FASTER
WHAT YOU GET
Summary for executive- and senior-level management
Technical details that include enough information to recreate our findings
Fact-based risk analysis to confirm a critical finding is relevant to the targeted environment
Tactical recommendations for immediate improvement
Strategic recommendations for longer-term improvement
ALL SERVICES
Consulting Services
within your budget.
Application Security Services
Achieve more-secure applications, compliant
environments, and safer systems development with
streamlined and repeatable processes.
Data Security Services
Protect your critical data across multiple environments,
meet privacy regulations and simplify operational
complexity.
Cloud Security Testing Services
Identify cloud vulnerabilities that tools alone cannot
find.
Security Risk Services
Secure your operations and respond to threats
with accuracy and speed.
Cloud Security Monitoring Services
deployments.
Get In Touch
If you have a more general question, connect with us by completing the form below and a member from our dedicated team will be in contact with you shortly.
General Contact
- +(1) 925 905 1280
- [email protected]
Registred Office
- 300 Delaware Ave, Suite 210, Wilmington, DE 19801
Corporate Office Office
- 111 Deerwood Road,Suite 200, San Ramon, CA 94583
Southern California
- 355 South Grand Ave, Suite 2450, Los Angeles, CA 90071

