Pentest Services
Can A Determined Attacker Gain Access to the Critical Assets You Cannot Afford to Have
Compromised?
Penetration Testing
We custom-tailor our services to your environment and needs. We assess specific aspects
of the security program and the state of security of your critical systems, networks and
applications. You can leverage intelligence gained from our years of experience and equip
yourself responding to the most sophisticated threat actors worldwide.

PENTEST 01
External Pentest
Identify and exploit vulnerabilities on systems, services and applications exposed to the Internet .

PENTEST 02
Internal Pentest
Simulate a malicious insider or an attacker that has gained access to an end-user system, including escalating privileges, installing custom-crafted malware or exfiltrating faux critical data

PENTEST 03
Web Application Pentest
Comprehensively assess web applications for vulnerabilities that can lead to unauthorized access or data exposure and develop a comprehensive framework for assessing the security of web-based applications.

PENTEST 04
External Pentest
Comprehensively assess the security of mobile devices and installed applications on on all mobile platforms, including iOS, Android, and Windows. Leverages OWASP Mobile Top 10 and methodologies to assess the security.

PENTEST 05
API Pentest
Comprehensively assess the security of API structures, understand request methods, understand responses and use techniques to apply to endpoints and exploit bugs on a real production

PENTEST 06
Wireless Pentest
Assess the security of your deployed wireless solution (e.g., 802.x, Bluetooth, Zigbee, etc.). AccessQuint's penetration testers attempt to exploit weaknesses in your network to gain access to privileged areas and demonstrate the potential impact of a wireless network breach.
EXTERNAL PENTEST
systems, services and applications
exposed to the Internet
OUR APPROACH
MITIGATING CYBER SECURITY RISKS WITH PENETRATION TESTS
Penetration test is a valuable part of comprehensive security program and can provide clear and concise direction on how to secure your critical infrastructure from real-world attacks and the potential risk of vulnerabilities. Security compliance best practices state that each organization should regularly test their information security program to ensure confidentiality, integrity, and availability of data.
- DISCOVERY AND SCOPE
- VULNERABILITY ASSESSMENT
- VULNERABILITY EXPOLITATION
- REMEDATION ASSITANCE
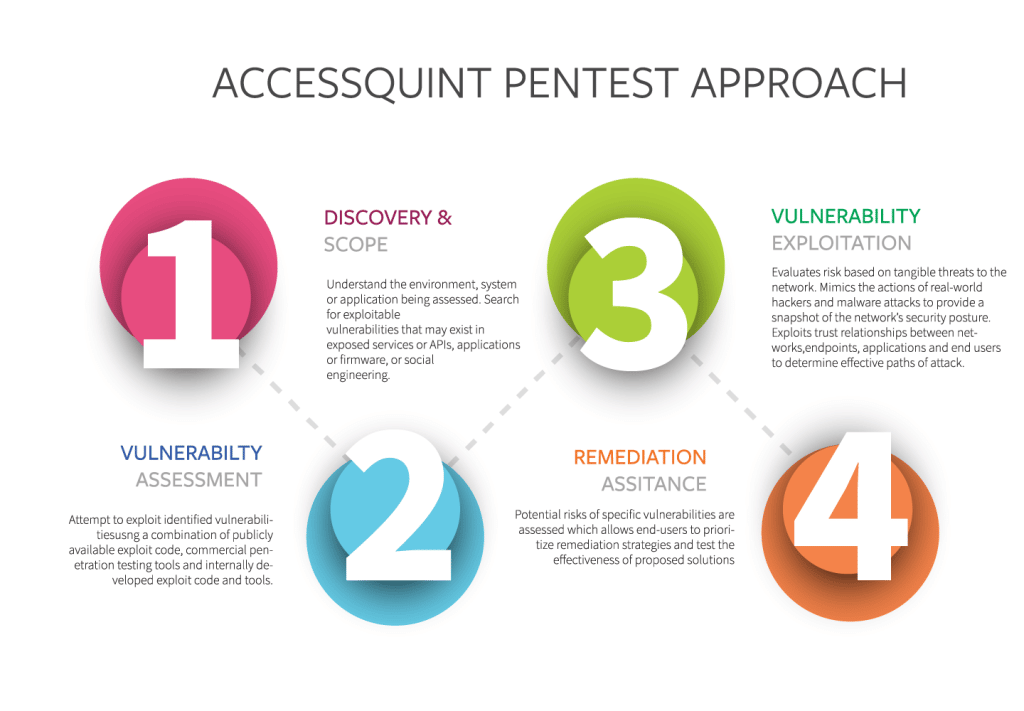
1 DISCOVERY & SCOPE
Understand the environment, system or application being assessed. Search for exploitable vulnerabilities that may exist in exposed services or APIs, applications or firmware, or social
2 VULNERABILTY EXPLOITATION
Attempt to exploit identified vulnerabilitiesusng a combination of publicly available exploit code, commercial penetration testing tools and internally developed exploit code and tools.
3 VULNERABILITY ASSESSMENT
Evaluates risk based on tangible threats to the network. Mimics the actions of real-world hackers and malware attacks to provide a snapshot of the network’s security posture.
4 REMEDIATION ASSITANCE
Potential risks of specific vulnerabilities are assessed which allows end-users to prioritize remediation strategies and test the effectiveness of proposed solutions
BUILD SECURE, HIGH-QUALITY SOFTWARE FASTER
BENEFITS
Know whether your critical assets are at risk
Identify and mitigate complex security vulnerabilities before an attacker exploits them
Understand how the most sophisticated attackers operate based on intelligence gained from our years performing incident response
Attain realistic findings and comprehensive recommendations


BUILD SECURE, HIGH-QUALITY SOFTWARE FASTER
WHAT YOU GET
Summary for executive- and senior-level management
Technical details that include enough information to recreate our findings
Fact-based risk analysis to confirm a critical finding is relevant to the targeted environment
Tactical recommendations for immediate improvement
Strategic recommendations for longer-term improvement
ALL SERVICES
Consulting Services
within your budget.
Application Security Services
Achieve more-secure applications, compliant
environments, and safer systems development with
streamlined and repeatable processes.
Data Security Services
Protect your critical data across multiple environments,
meet privacy regulations and simplify operational
complexity.
Cloud Security Testing Services
Identify cloud vulnerabilities that tools alone cannot
find.
Security Risk Services
Secure your operations and respond to threats
with accuracy and speed.
Cloud Security Monitoring Services
deployments.
Get In Touch
If you have a more general question, connect with us by completing the form below and a member from our dedicated team will be in contact with you shortly.
General Contact
- +(1) 925 905 1280
- [email protected]
Registered Office
- 300 Delaware Ave, Suite 210, Wilmington, DE 19801
Corporate Office
- 4900 Hopyard Rd, Suite 100, Pleasanton, CA 94588
-
111 Deerwood Road,Suite 200,
San Ramon, CA 94583

